TalkTalk is facing renewed calls to improve its cybersecurity after an anonymous hacker contacted Sky News about a website flaw that went unfixed for years.
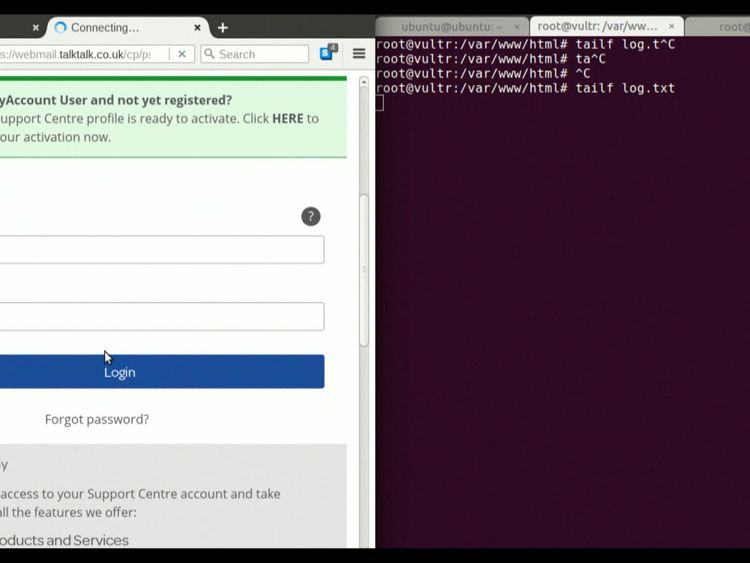
The hacker – known as "B" – found a "Cross Site Scripting" error allowing him to take control of a convincing looking "talktalk.co.uk" URL, which meant he could potentially trick any of the company's webmail customers into thinking they were accessing an official TalkTalk website.
He then showed us through a secure demonstration how easy it would be to steal a victim's login details, and any other sensitive information, if he could get the individual to click on the link.
This could be done, he suggests, through targeting customers with email phishing techniques, or by circulating his own link around tech support forums or social media.
TalkTalk fixed the flaw this week after Sky News got in touch, but it has come to light that the company was first alerted to the bug through a so-called "bug bounty" platform in March 2016.
Bug bounties are rewards or cash given to hackers who alert companies that their website is vulnerable to attack.
Speaking before the flaw was fixed, the hacker told Sky News: "The vulnerability is worryingly easy to locate. The vulnerable page and parameters can be identified within seconds of looking at the website.
"After initially identifying it, we also discovered that it was submitted to a bug bounty platform in 2016. Relevant notification was issued to TalkTalk and we've made multiple attempts to get them to fix it.
"What I can't understand is why such neglect is applied to TalkTalk's website security. TalkTalk's website has a history of vulnerabilities. One would assume that after the attack in 2015, they would pay more attention to the state of their security."
The company was given a record £400,000 fine by the Information Commissioner's Office after the major breach in October 2015, during which 157,000 customer details were stolen, including some bank details.
The firm was told to "be more diligent and more vigilant", and was fined a further £100,000 after data belonging to 21,000 customers was exposed to "rogue" staff at a call centre in India.
The company admits that it knew about this latest security flaw but deemed the risk low enough to leave it un-patched.
For some in the cybersecurity sector, the flaw should have been fixed no matter how low the perceived risk.
Matthew Hickey, co-founder of Hacker House consultancy, said: "I believe if somebody is masquerading information as though it comes from TalkTalk, then they have an obligation to protect their brand.
"Consumer security is an important aspect and if we can get organisations to care about the consumer security model, then it would also hint that they care internally about their own security model."
A TalkTalk spokesman told Sky News there was "no evidence to suggest that any customers were affected" by the "theoretical issue", which they said had been resolved.
They continued: "We of course take all security issues very seriously. Like any phishing attempt, customers would only be exposed if they were sent and followed a malicious web address.
"We regularly advise customers about the dangers of following links in phishing emails and we provide customers with free, industry-leading tools to protect against relevant viruses and malware.
More from Science & Tech
"We will shortly be completing a major upgrade of our email service for all customers. In the meantime, customers should continue to access their webmail services normally."
The hacker confirmed that the flaw is fixed and says he is happy to have helped the company overcome the security problem before it was exploited.
[contf] [contfnew] 
Sky News
[contfnewc] [contfnewc]







