In late December, Google and Apple removed the ToTok social messaging app from their marketplaces after US intelligence officials told The New York Times it was a tool for surreptitious spying by the United Arab Emirates government. About a week later, Google reinstated the Android version of the app with no explanation, a move that confounded app users and security experts. Now Google has once again baffled industry watchers by once again banishing the app without saying why. (Apple, meanwhile, has continued to keep the iOS version of ToTok out of the App Store.)
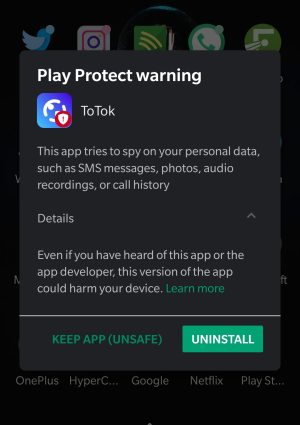
Over the past few days, Play Protect, the Google service that scans Android devices for apps that violate the companys terms of service, started displaying a warning that says: “This app tries to spy on your personal data, such as SMS messages, photos, audio recordings, or call history. Even if you have heard of this app or the app developer, this version of the app could harm your device.”
The message, displayed to the right, then gives the user the option to either “uninstall” or “keep app (unsafe).”
Google has declined to comment to me or any other reporters seeking the reason for this strange series of back-and-forth moves. In the vacuum, commentators have offered all kinds of theories for Googles rationale.
“Is this where the tinfoil hat of rampant speculation comes out?” asked information security professional Ben Montour on Twitter. “UAE friendly insider on app approval team? Allowed it back, was caught and it was pulled again?”
@Metacurity @Bing_Chris Is this where the tinfoil hat of rampant speculation comes out? UAE friendly insider on app approval team? Allowed it back, was caught and it was pulled again?
— Ben Montour (@benmontour) February 20, 2020
Ill be watching you
In the months leading up its initial removal, ToTok received millions of downloads from Play and the App Store combined. The iOS app alone had more than 32,000 user reviews, most of them favorable. Its possible many of the downloads and reviews were part of a UAE-sponsored astroturf campaign designed to increase the favorable visibility of the app, but its likely much of the popularity was genuine. The UAE government had already restricted use of rival apps, such as Skype and WhatsApp, a move that made ToTok more appealing to those communicating with people inside the country.
The initial removals by Google and Apple came within days of the New York Times article, which said the UAE government was using ToTok to “try to track every conversation, movement, relationship, appointment, sound, and image of those who install it on their phones.”
An independent analysis by macOS and iOS security expert Patrick Wardle confirmed that the iOS-version of ToTok did in fact collect the entire address book and upload it to a server connected to the ToTok domain. That activity happened only when users gave the app permission to access their contacts, but granting such rights is an expected and standard practice for those using messaging apps.
“Basically [app developers] didn't have to add any malicious code to the app (on the phone),” Wardle, who is a security researcher at the macOS and iOS enterprise management firm Jamf, told me on Thursday. “Just ban all other apps in the UAE, offer a free alternative, push it via the (state) media/fake reviews and make sure all in-app comms (msgs, videos, images, etc. etc.) are routed through their servers (with no E2E encryption). Then once you identify targets/ppl of interest, you throw/use your iOS/Android 0days against just those handful of targets. It's really a lovely approach… well, from their point of view.”
A zeroday is an attack that exploits a software vulnerability thats unknown to the developer. Weaponized zeroday exploits—meaning they reliably and stealthily hack devices and arent easily detected—often cost large sums of money. The UAE has been suspected of using an expensive iOS zeroday in 2016 in an attempt to hack the iPhone of a political dissident in that country.
“Resolute in our innocenceRead More – Source [contf] [contfnew] 
arstechnica
[contfnewc] [contfnewc]





