Malicious hackers are mass exploiting a critical vulnerability in D-Link DSL routers in an attempt to make them part of Satori, the potent Internet-of-things botnet thats used to take down websites and mine digital coins, researchers said.
Since making its debut late last year, Satori has proven to be a particularly versatile and sophisticated botnet. It made a name for itself in December when it infected more than 100,000 Internet-connected devices in just 12 hours by exploiting remote code-execution vulnerabilities in Huawei and RealTek routers. A month later, Satori operators released a new version that infected devices used to mine digital coins, proving that the IoT botnet could also take control of more traditional computing devices. In February, Satori resurfaced when it infected tens of thousands of routers manufactured by Dasan Networks.
Building a better mousetrap
A key to Satoris success is its use of the publicly released Mirai IoT botnet source code to turn devices with easily guessable passwords into platforms for launching Internet-crippling attacks. In 2016, Mirai launched a series of record-setting denial-of-service attacks that took security site KrebsonSecurity offline and also targeted online gamers. Satori operators use the Mirai code as a foundation on which theyve erected an evolving series of new exploits that allow the botnet to control devices even when theyre secured with strong passwords.
Over the past five days, researchers said, Satori has started mass exploiting a critical vulnerability in the D-Link DSL 2750B, a combination router and DSL modem thats used by subscribers of Verizon and other ISPs. Attack code exploiting the two-year-old remote code-execution vulnerability was published last month, although Satoris customized payload delivers a worm. That means infections can spread from device to device with no end-user interaction required. D-Links website doesnt show a patch being available for the unindexed vulnerability, and D-Link representatives didnt respond to an email seeking comment for this post.
Researchers with Netlab 360 first reported Satori was exploiting the D-Link vulnerability in a blog post published Friday. They also said Satori had started exploiting a vulnerability in a router made by XiongMai. On Tuesday, researchers from Radware reported seeing an “exponential increase in the number of attack sources” for attacks on both the D-Link and XiongMai devices.
“Radwares Threat Research team witnessed thousands of IPs trying to infect our honeypots at a high rate using a previously unseen payload,” the researchers wrote in a blog post. The attack targeting the D-Link routers causes them to send a wget command that downloads a remote script hosted on a Web server at 185.62.190.191. The US represented the fourth-most-affected country, behind Brazil, the Republic of Korea, and Italy.
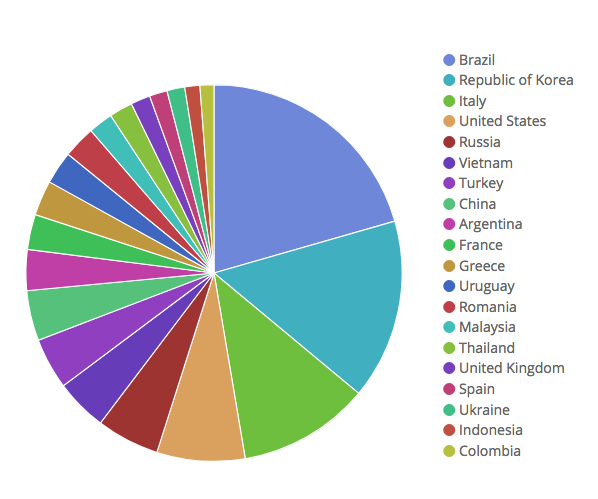
Radware said the vulnerability was disclosed no later than 2016. This D-Link page shows the most recent firmware version for the device was released in 2015.
The exploits come a month after researchers disclosed the existence of malware developed by Russian spies that has infected more than 500,000 routers from a variety of manufacturers. Dubbed VPNFilter, the malware isnt believed to have any connection to Satori. Neither the D-Link DSL-2750B nor the XiongMai device is included on the list of routers known to be targeted by VPNFilter.
Its not immediately clear what people with a vulnerable D-Link device can do to protect themselves from these attacks. Ars has asked both D-Link and Radware to provide guidance. In the meantime, people using one should strongly consider replacing it.
[contf] [contfnew] 
Ars Technica
[contfnewc] [contfnewc]







