Emotet, the worlds most costly and destructive botnet, returned from a five-month hiatus on Friday with a blast of malicious spam aimed at spreading a backdoor that installs ransomware, bank-fraud trojans, and other nasty malware.
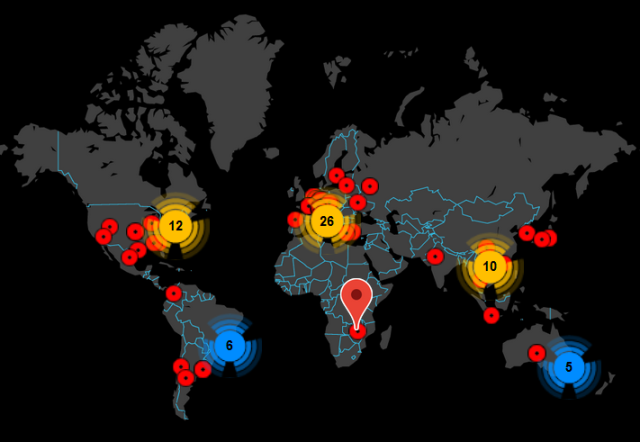
The botnet sent a hefty 250,000 messages during the day, mostly to people in the United States and the United Kingdom, Sherrod DeGrippo, senior director of threat research and detection at security firm Proofpoint, told Ars. Other researchers said targets were also located in the Middle East, South America, and Africa. The botnet followed its characteristic pattern of sending either a malicious document or link to a malicious file that, when activated, installs the Emotet backdoor.
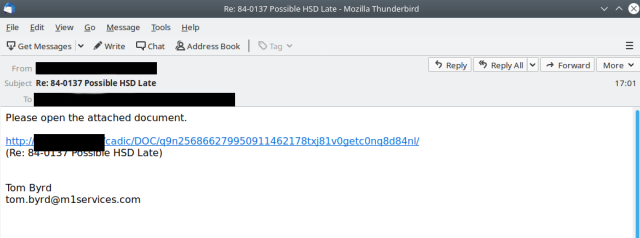
The botnet gave its first indications of a return on Tuesday, with small message volumes being sent out. Email samples that appeared on Twitter accounts from threat monitors abuse.ch and Spamhaus looked like this:
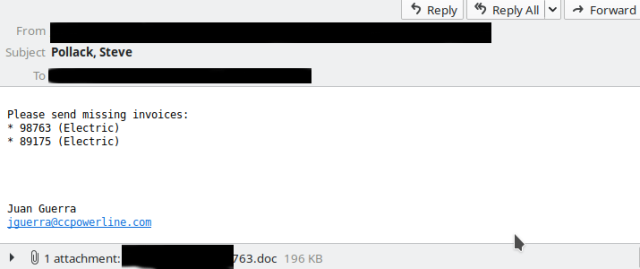
Emotets resurgence on Friday was also spotted by antivirus provider Malwarebytes and Microsoft.
Box of tricks
Emotet has proven to be one of the more resourceful threats to face people in recent years. Emails often appear to arrive from a person the target has corresponded with in the past. The malicious messages often use the subject lines and the bodies of previous email threads the two have participated in. Emotet gets this information by collecting the contact lists and inboxes of infected computers.
The technique has a dual benefit. It tricks the target into thinking the message can be trusted because it comes from a known friend, acquaintance, or business associate who is following up on a previously discussed matter. The inclusion of authentic content also makes it harder for spam filters to detect the emails as malicious.
Another of Emotets clever tricks: it steals usernames and passwords for outgoing email servers. The botnet then uses the credentials to send mail from those servers rather than relying on its own infrastructure. Because the trusted servers send the malicious messages, theyre harder for security products to detect and block.
Hit and run
DeGrippo said that the last time Emotet had shown itself was during a five-day run in early February, that delivered about 1.8 million messages. The botnet is known for making big blasts for short periods of time and then going silent for weeks or months at a time. Last September, it woke from a four-month slumber.
The group is known for taking long breaks and regularly taking time off during weekends and major holiday seasons. True to its normal pattern, the latest Emotet activity had completely stopped oRead More – Source
[contf] [contfnew] 
arstechnica
[contfnewc] [contfnewc]







