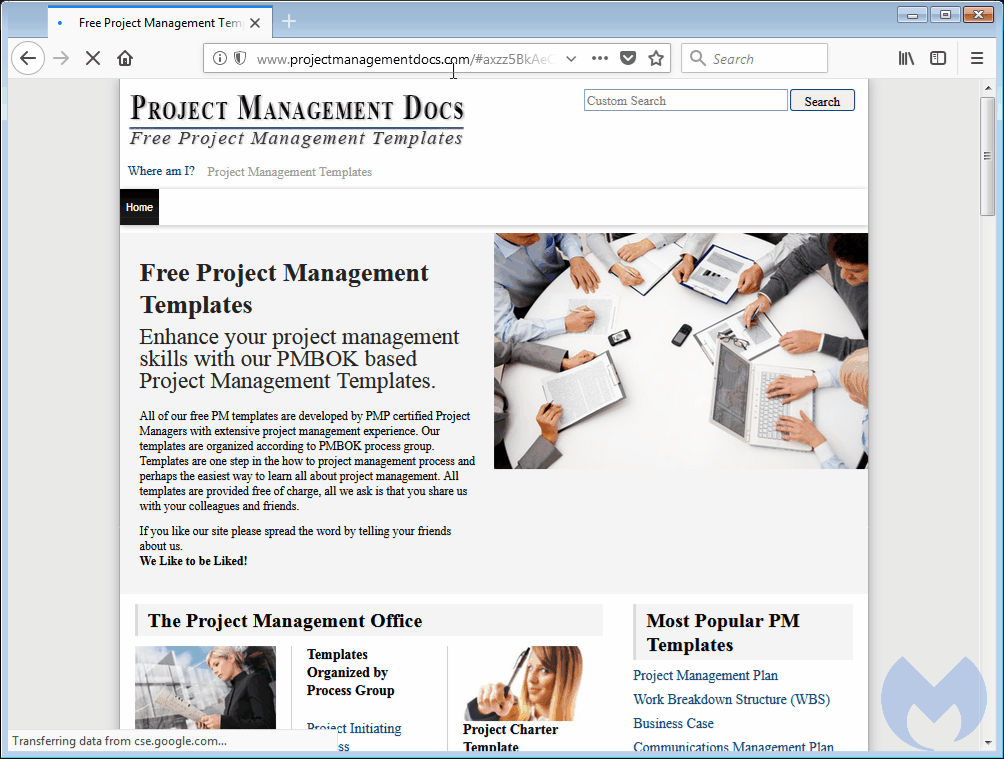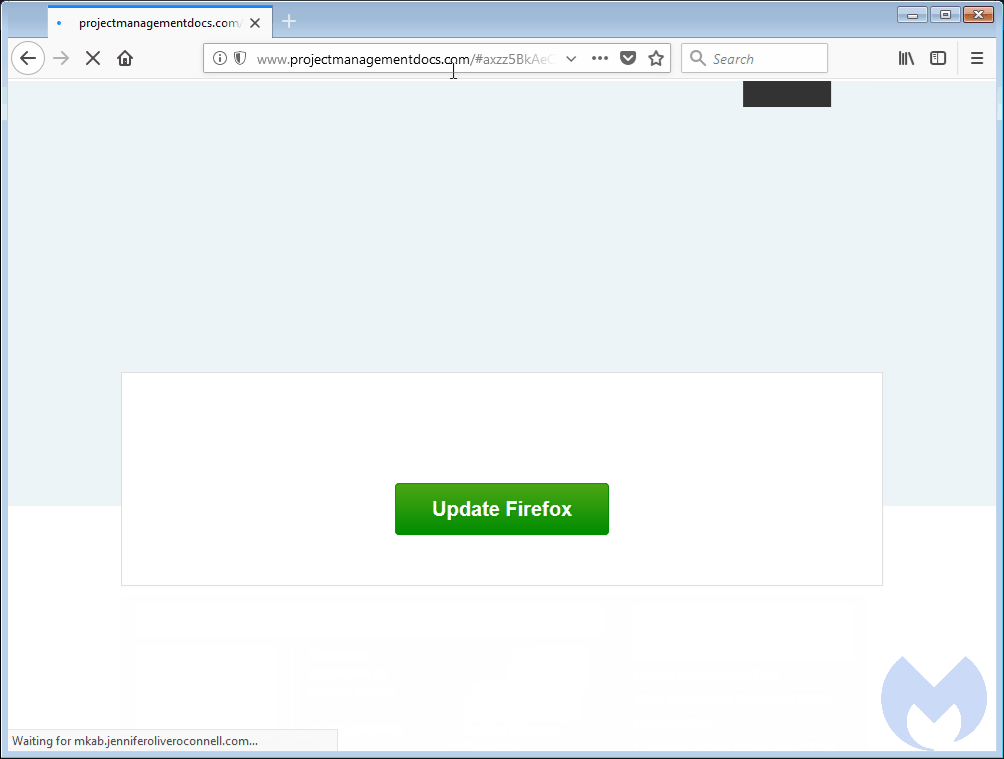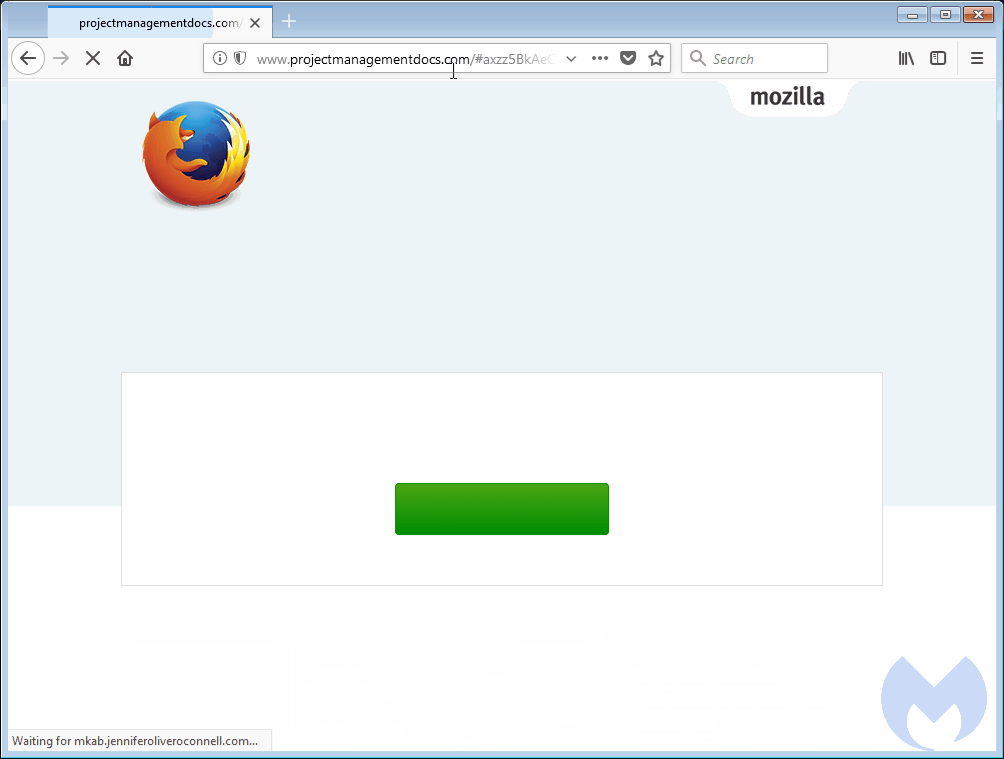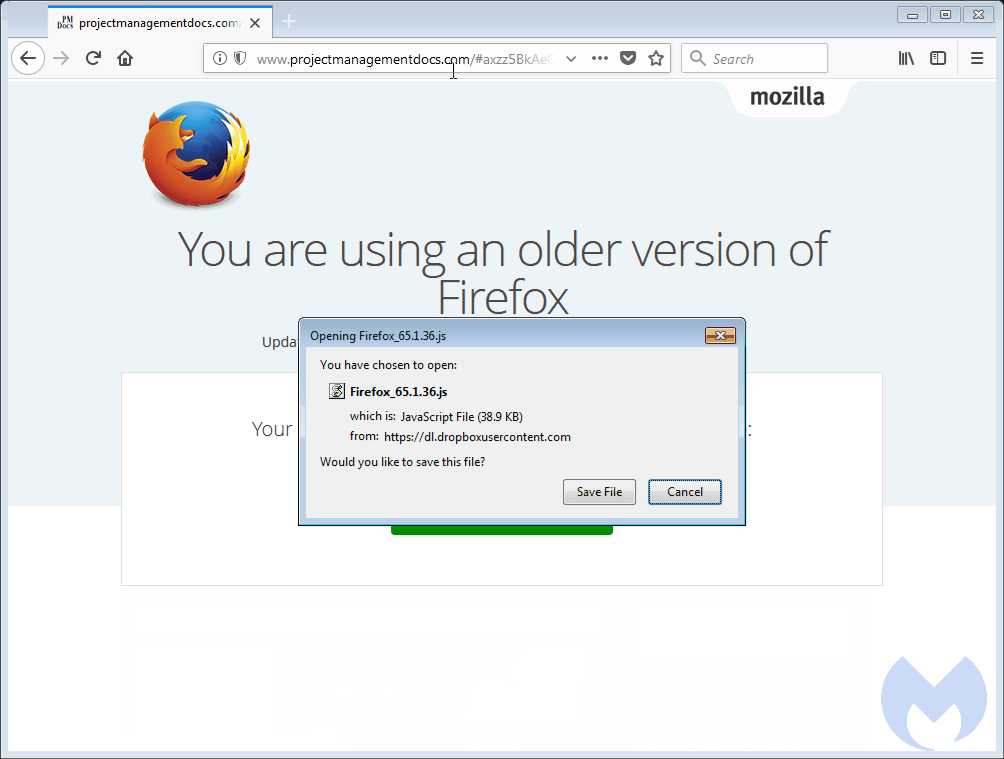
Thousands of hacked websites have become unwitting participants in an advanced scheme that uses fake update notifications to install banking malware and remote access trojans on visitors' computers, a computer researcher said Tuesday.
The campaign, which has been running for at least four months, is able to compromise websites running a variety of content management systems, including WordPress, Joomla, and SquareSpace. That's according to a blog post by Jérôme Segura, lead malware intelligence analyst at Malwarebytes. The hackers, he wrote, cause the sites to display authentic-appearing messages to a narrowly targeted number of visitors that, depending on the browsers they're using, instruct them to install updates for Firefox, Chrome, or Flash.
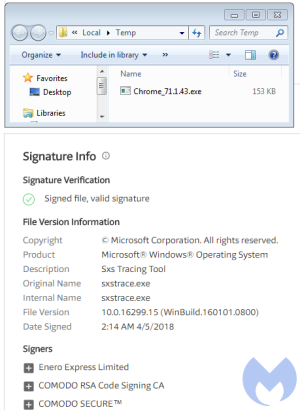
To escape detection, the attackers fingerprint potential targets to ensure, among other things, that the fake update notifications are served to a single IP address no more than once. Another testament to the attackers' resourcefulness: the update templates are hosted on hacked websites, while the carefully selected targets who fall for the scam download a malicious JavaScript file from DropBox. The JavaScript further checks potential marks for virtual machines and sandboxes before delivering its final payload. The resulting executable file is signed by an operating-system-trusted digital certificate that further gives the fake notifications the appearance of legitimacy.
"This campaign relies on a delivery mechanism that leverages social engineering and abuses a legitimate file-hosting service," Segura wrote. "The 'bait' file consists of a script rather than a malicious executable, giving the attackers the flexibility to develop interesting obfuscation and fingerprinting techniques."
Flying under the radar
The attackers also fly under the radar by using highly obfuscated JavaScript. Among the malicious software installed in the campaign was the Chthonic banking malware and a commercial remote access trojan known as NetSupport.
Malwarebytes was unable to determine precisely how many sites have been compromised. Using a simple crawler script, researchers identified several hundred compromised WordPress and Joomla sites, leading them to estimate there were thousands of such infections. This query on source code search engine PublicWWW revealed slightly more than 900 infected SquareSpace sites earlier Tuesday. At the time this post went live, the number had fallen to 774. This post from independent security researcher BroadAnalysis shows the campaign started no later than December 20. The sites were hacked because operators failed to install available security updates or possibly didn't follow other basic security measures, Segura said.
Other Internet posts show the campaign in action as well. This Twitter thread from last month documents two compromised SquareSpace sites. A February 28 post on a SquareSpace support forum reports yet another compromise, with another site maintainer experiencing the same thing almost two weeks later.
Campaigns that use compromised websites to prey on visitors have grown increasingly common over the past decade. Typically, they're used in computer support scams that try to trick people into paying to fix nonexistent computer problems. More recently, compromised websites have been used to install ransomware or malware that surreptitiously mines cryptocurrency. The ability for this fake update scam to remain hidden for at least four months, coupled with its embrace of banking malware and backdoor Trojans, makes it stand out.
"The cloaking used in this campaign is what drew our attention because it sets it apart from other infection chains that are much less sophisticated and easier to identify and block," Segura told Ars. "Another interesting aspect is the fact that such fake updates are typically distributed via malvertising, which is usually cheaper. As of recently, one of the more popular payloads from compromised sites was the tech support scams via browser lockers. We are starting to see a trend for much more serious malware, such as stealers and remote administration tools in this case."
[contf] [contfnew] 
Ars Technica
[contfnewc] [contfnewc]







