For decades, the use of fingerprints to authenticate users to computers, networks, and restricted areas was (with a few notable exceptions) mostly limited to large and well-resourced organizations that used specialized and expensive equipment. That all changed in 2013 when Apple introduced TouchID. Within a few years, fingerprint-based validation became available to the masses as computer, phone, and lock manufacturers added sensors that gave users an alternative to passwords when unlocking the devices.
Although hackers managed to defeat TouchID with a fake fingerprint less than 48 hours after the technology was rolled out in the iPhone 5S, fingerprint-based authentication over the past few years has become much harder to defeat. Today, fingerprints are widely accepted as a safe alternative over passwords when unlocking devices in many, but not all, contexts.
A very high probability
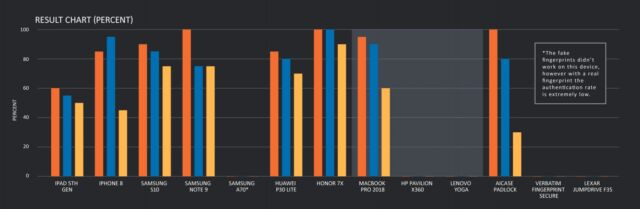
A study published on Wednesday by Ciscos Talos security group makes clear that the alternative isnt suitable for everyone—namely those who may be targeted by nation-sponsored hackers or other skilled, well-financed, and determined attack groups. The researchers spent about $2,000 over several months testing fingerprint authentication offered by Apple, Microsoft, Samsung, Huawei, and three lock makers. The result: on average, fake fingerprints were able to bypass sensors at least once roughly 80 percent of the time.
The percentages are based on 20 attempts for each device with the best fake fingerprint the researchers were able to create. The results may not be fully applicable to Apple products since they limit users to five attempts before asking for the PIN or password. Other products tested permitted significantly more or even an unlimited number of unsuccessful tries.
Tuesdays report was quick to point out that the results required several months of painstaking work, with more than 50 fingerprint molds created before getting one to work. The study also noted that the demands of the attack—which involved obtaining a clean image of a targets fingerprint and then getting physical access to the targets device—meant that only the most determined and capable adversaries would succeed.
“Even so, this level of success rate means that we have a very high probability of unlocking any of the tested devices before it falls back into the PIN unlocking," Talos researchers Paul Rascagneres and Vitor Ventura wrote. “The results show fingerprints are good enough to protect the average person's privacy if they lose their phone. However, a person that is likely to be targeted by a well-funded and motivated actor should not use fingerprint authentication.”
The devices that were the most susceptible to fake fingerprints were the AICase padlock and Huaweis Honor 7x and Samsungs Note 9 Android phones, all of which were bypassed 100 percent of the time. Fingerprint authentication in the iPhone 8, MacBook Pro 2018, and the Samsung S10 came next, where the success rate was more than 90 percent. Five laptop models running Windows 10 and two USB drives—the Verbatim Fingerprint Secure and the Lexar Jumpdrive F35—performed the best, with researchers achieving a 0-percent success rate.
The chart below summarizes the results:
The reason for the better results from the Windows 10 machines, the researchers said, is that the comparison algorithm for all of them resided in the OS, and therefore the result was shared among all platforms. The researchers cautioned against concluding that the zero success-rate for Windows 10 devices and the USB drives meant they were safer.
“We estimate that with a larger budget, more resources and a team dedicated to this task, it is possible to bypass these systems, too,” they wrote.
One other product tested—a Samsung A70—also attained a 0-percent failure rate, but researchers attributed this to the difficulty getting authentication to work even when it received input from real fingerprints that had been enrolled.
Defeating fingerprint authentication: A how-to
There are two steps to fingerprint authentication: capturing, in which a sensor generates an image of the fingerprint, and analysis that compares the imputted fingerprint to the fingerprint thats enrolled. Some devices use firmware that runs on the sensor to perform the comparison while others rely on the operating system. Windows Hello included in Windows 10, for example, performs the comparison from the OS using Microsofts Biometric Devices Design Guide.
There are three types of sensors. Capacitive sensors use a fingers natural electrical conductivity to read prints, as ridges touch the reader while valleys do not. Optical sensors read the image of a fingerprint by using a light source that illuminates ridges in contact with the reader and reads them through a prism. Ultrasonic sensors emit an ultrasonic pulse that generates an echo thats read by the sensor, with ridges and valleys registering different signatures.
The researchers devised three techniques for collecting the fingerprint of a target. The first is direct collection, which involves a target pressing a finger on a brand of clay known as Plastiline. With that, the attacker obtains a negative of the fingerprint. The second technique is to have the target press a finger onto a fingerprint reader, such as the kind thats used at airports, banks, and border crossings. The reader would then capture a bitmap image of the print. The third is to capture a print on a drinking glass or other transparent surface and take a photograph of it.
After the print is collected using the print reader or photo methods, certain optimizations are often required. For prints recorded on a fingerprint reader, for instance, multiple images had to be merged together to create a single image that was large enough to pass for a real fingerprint. Below is an example of the process, performed on fingerprints the FBI obtained from prohibition-era gangster Al Capone.

Prints captured on a glass and then photographed, meanwhile, had to be touched up with filters to increase the contrast. Then the researchers used digital sculpting tools such as ZBrush to create a 3D model based on the 2D picture.

Once the fingerprint was collected from either a scanner or glass and then optimized, the researchers replicated them onto a mold, which was made from either fabric glue or silicon. When working against capacitive sensorsRead More – Source
[contf] [contfnew] 
arstechnica
[contfnewc] [contfnewc]







